Team!
Two days ago VMware announced that vSphere 7.0 Update 2 is now generally available! This release is packed with a bunch of great features, as always! There’s one the really hit home with me too. I’ve already had a few discussions with some people about it and, for me, the introduction of the Native Key Provider is a true homerun for everyone, especially Enterprise Plus license users.
What is a Key Provider/Management Server?
In a nutshell, a Key Management Server (KMS) is an infrastructure (I say infrastructure because you’ll want to ensure this is secured and highly available) that is used to generate, and hold/secure cryptography keys used in your environment and protect them against loss or even misuse. A great article that goes into depth about KMSes can be found here.
Why Do I Even Need One?
Security. Whether it’s in the forefront of your mind or it’s a little whisper in the back of your head, today it is required and extremely prevalent in almost every IT-related conversation. Data encryption and privacy concerns have skyrocketed, which means the use of data encryption has too. In VMware, to be able to perform any vSAN data store or VM-level encryption an KMS was required. Until 7.0U2 that meant you had to purchase a third-party solution and I’ve seen companies spend a MINIMUM of $20-$40k on KMS appliances. Well, if you upgrade to vSphere 7.0U2 then that reliance on third-party solutions is officially broken. If you already have a KMS I would highly recommend continuing to use it. The Native Key Provider isn’t particularly here to replace the function of a dedicated KMS, but more so to be able to provide companies a foot-in-the-door with data encryption from VMware’s perspective.
Sold! Show Me the Ways!
If you have already upgraded vCenter and ESXi to 7.0U2, the process to add and start using the Native Key Provider is extremely simple. First, select the vCenter object from the ‘Hosts and Clusters’ view:
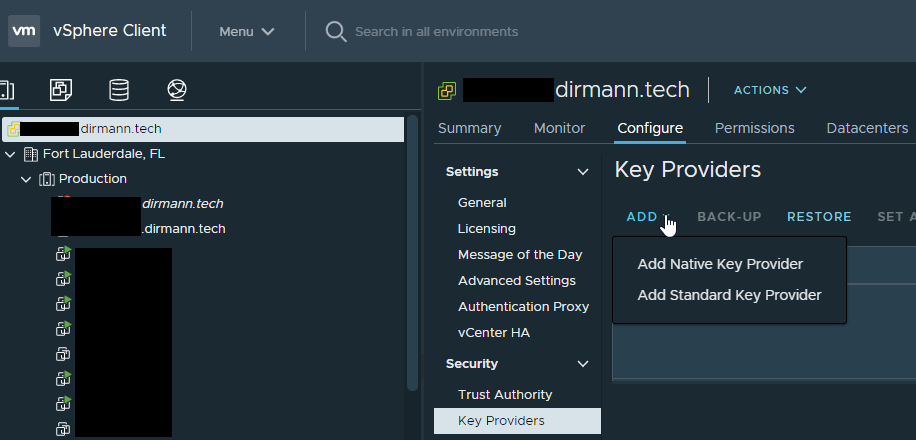
Next, give the NKP a meaningful name. If you want the NKP to be available to only hosts with TPMs installed, then check off the box and click ‘Add Key Provider’. I don’t have TPMs (but they are on order) and highly recommended. They are usually only about $50 per server, if supported):

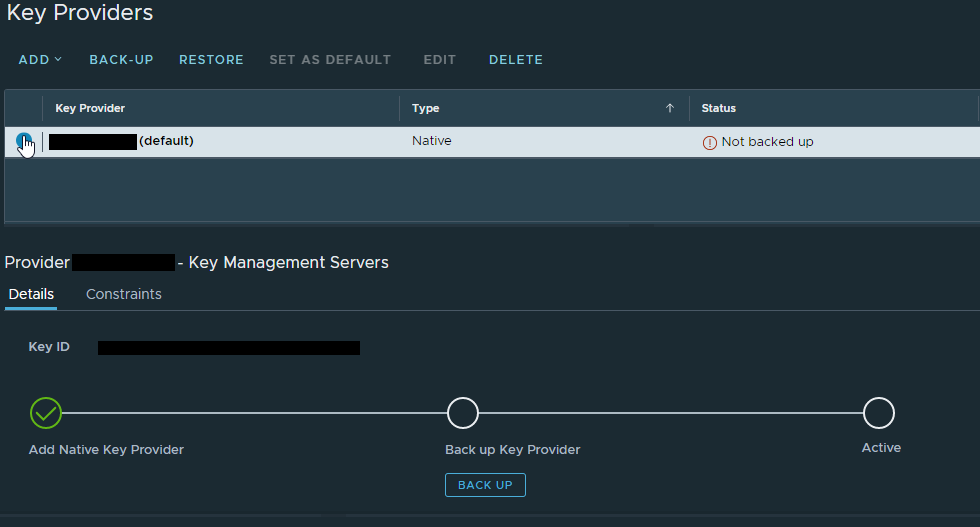
Before you can use the NKP, you must back it up by clicking none other than ‘Backup’.
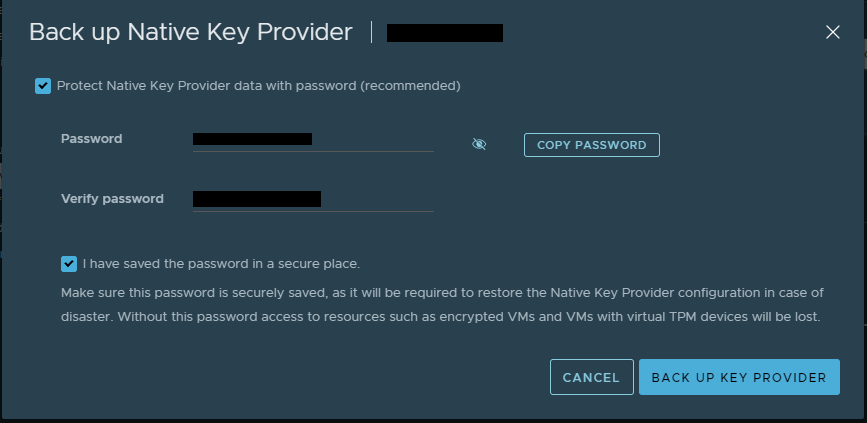
Let’s go ahead and give this backup a password. No sense in backing up security with no security in place. Check the box, provide the password, acknowledge that you have recorded the password in a secure location and click ‘Back Up Key Provider’. This will download the backup in PKCS #12 format. Save the file some place secure, limit who has access to it, get auditing enabled. Remember, this is now the key to your castle regarding encryption.
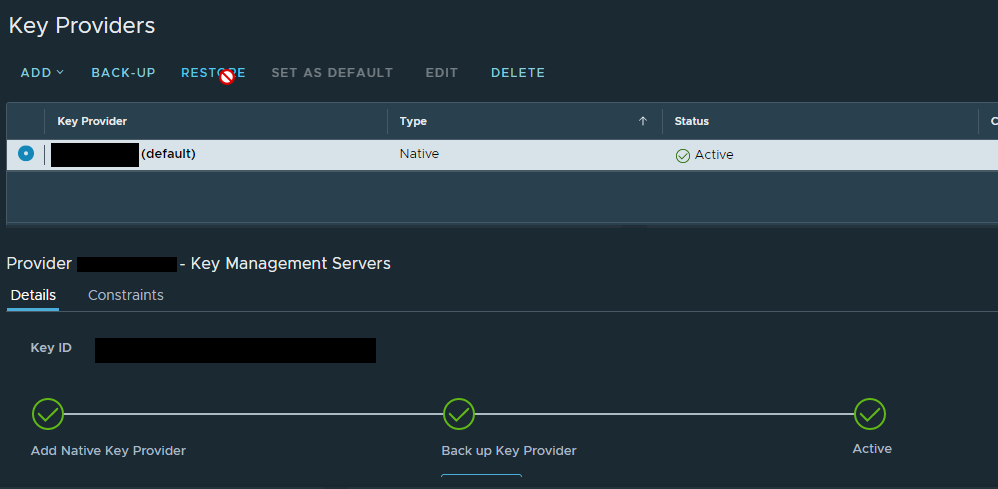
Depending on the size of the environment, it could take a few minutes for the NKP to become active and available for use, but it looks like this you’re ready to go:
Let’s encrypt some VMs! vCenter comes with a pre-packaged VM encryption policy, which is ironically named ‘VM Encryption Policy’. You can create one to tweak some of the few settings available in the policy, but for this case we’re just going to use the built-in policy.
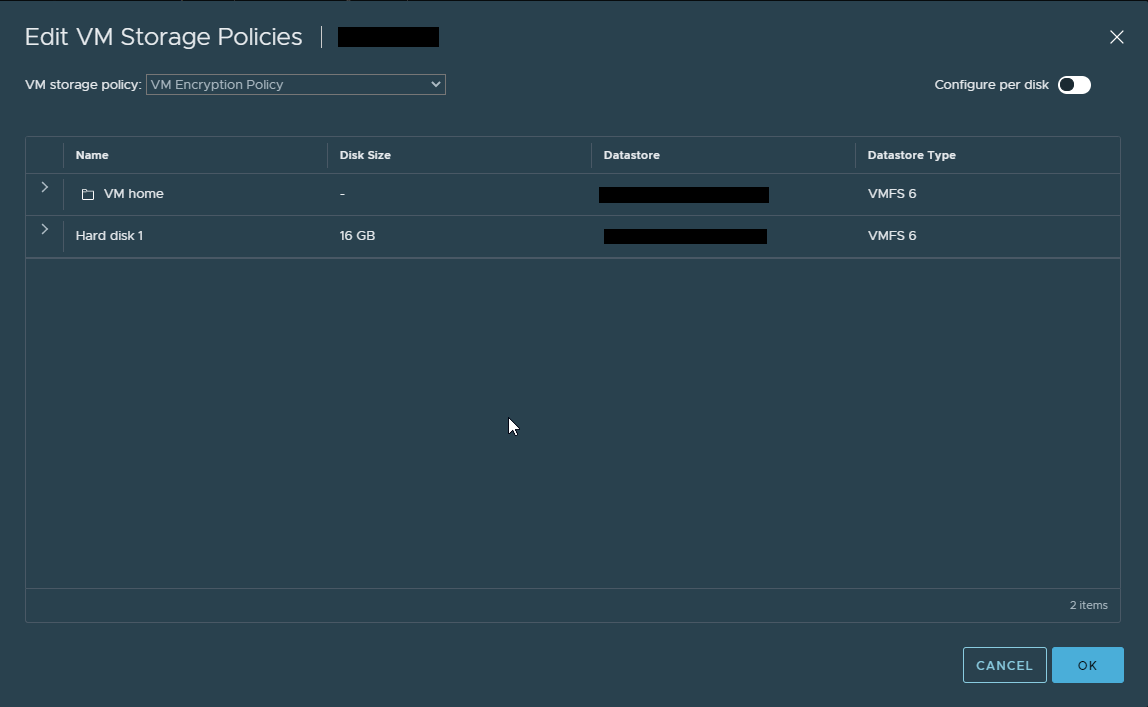
Select the ‘VM Encryption Policy’ from the drop down, and either click ‘OK’ to apply, or ‘Configure per disk’ if you want to get granular with the application:
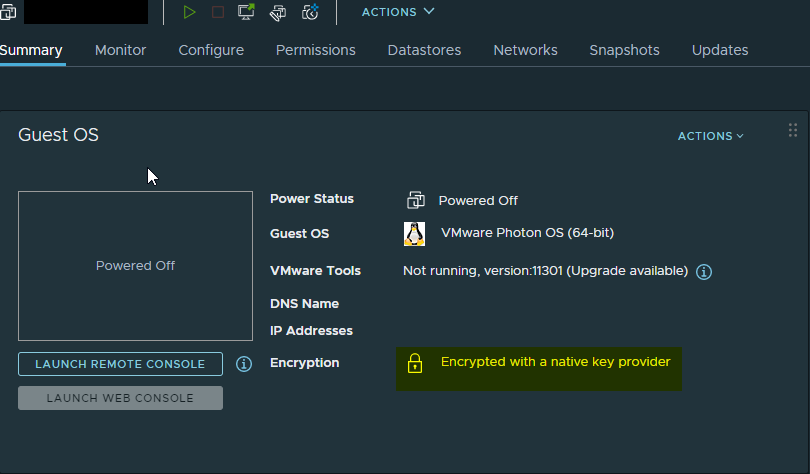
Depending on the size of the VM it may take some time for VMware to do their magic, but the result is a freshly encrypted VM:
Conclusion
There are a lot of nice features in the 7.0U2 release, but today we discussed the addition of the Native Key Provider and how to use it for VM-level encryption. We also walked you through configuring the NKP and using it to encrypt your VMs. Thanks for reading. If you enjoyed the post make sure you check us out at dirmann.tech and follow us on LinkedIn, Twitter, Instagram, and Facebook!
References:
https://docs.vmware.com/en/VMware-vSphere/7.0/rn/vsphere-vcenter-server-702-release-notes.html
https://blog.ariacybersecurity.com/blog/encryption-key-management-blog

Paul Dirmann (vExpert PRO*, vExpert***, VCIX-DCV, VCAP-DCV Design, VCAP-DCV Deploy, VCP-DCV, VCA-DBT, C|EH, MCSA, MCTS, MCP, CIOS, Network+, A+) is the owner and current Lead Consultant at Dirmann Technology Consultants. A technology evangelist, Dirmann has held both leadership positions, as well as technical ones architecting and engineering solutions for multiple multi-million dollar enterprises. While knowledgeable in the majority of the facets involved in the information technology realm, Dirmann honed his expertise in VMware’s line of solutions with a primary focus in hyper-converged infrastructure (HCI) and software-defined data centers (SDDC), server infrastructure, and automation. Read more about Paul Dirmann here, or visit his LinkedIn profile.
